GENERAL
road map for a vulnerability management team medium
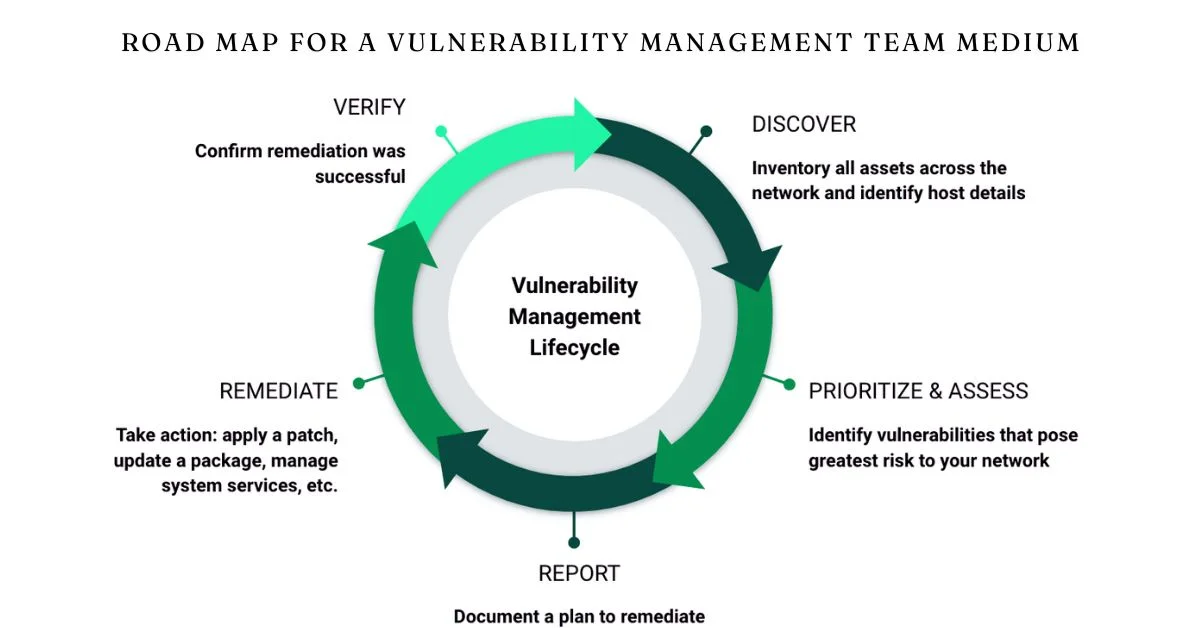
Introduction to road map for a vulnerability management team medium
In today’s digital landscape, the importance of a robust vulnerability management team cannot be overstated. As cyber threats evolve and become more sophisticated, organizations must stay one step ahead to safeguard their assets. A well-structured road map for a vulnerability management team medium provides that crucial direction. It lays out clear strategies, responsibilities, and best practices to navigate the complexities of identifying and mitigating vulnerabilities effectively.
Imagine having a detailed plan in place that not only addresses current weaknesses but also anticipates future challenges. This blog post will explore how to develop an effective road map tailored specifically for your team’s needs while enhancing collaboration and communication along the way. Join us as we delve into the key components essential for building an exceptional vulnerability management program that stands resilient against ever-changing threats!
ALSO READ: Predovac: Innovating the Education Landscape
Understanding the Role of road map for a vulnerability management team medium
A well-defined road map for a vulnerability management team medium acts as both a guide and blueprint. It outlines the strategic direction, ensuring everyone understands their roles and responsibilities.
The role of this road map is multifaceted. First, it prioritizes vulnerabilities based on risk levels, allowing teams to focus on what matters most.
This approach helps in resource allocation—ensuring that time and effort target the highest risks rather than spreading resources too thinly across less critical issues.
Moreover, it fosters alignment within the team by setting clear objectives and timelines. This clarity enhances accountability among members while reducing redundancy.
Having a structured plan aids in adapting to new threats or changes within an organization’s infrastructure swiftly. A responsive strategy keeps security measures relevant amidst evolving cyber landscapes.
Key Responsibilities of a Vulnerability Management Team
A vulnerability management team plays a crucial role in safeguarding an organization’s assets. Their first responsibility is to identify vulnerabilities across all systems. This involves continuous scanning, assessing risks, and prioritizing issues based on potential impact.
Next comes remediation. The team collaborates with IT departments to ensure that identified vulnerabilities are addressed swiftly and effectively. They provide guidance on patch management and system updates.
Monitoring is another key task. After remediation, the team must analyze whether fixes have been successful or if further action is necessary.
Reporting also falls under their purview. Regular updates for stakeholders keep everyone informed of the current security posture and any emerging threats.
Training employees about best practices in cybersecurity rounds out their responsibilities, fostering a culture of security awareness throughout the organization.
ALSO READ: Everything about pinterest engineering blog experiments
Developing a road map for a vulnerability management team medium
Creating a road map for a vulnerability management team requires careful planning and strategic thinking. Start by defining the team’s goals. Prioritize what needs immediate attention versus what can be addressed later.
Next, assess your current vulnerabilities and resources. This assessment will inform your team’s capacity to tackle threats effectively. Identify tools that support automation and streamline processes.
Establish clear timelines for each phase of the plan. Short-term milestones build momentum, while long-term objectives keep everyone focused on broader targets.
Involve key stakeholders early in the process to ensure alignment across departments. Regular feedback loops are essential for adapting strategies as new threats emerge or organizational priorities shift.
Document every step taken along this journey. A transparent record not only tracks progress but also helps refine future initiatives.
Best Practices for Implementing and Maintaining a Successful Vulnerability Management Program
Implementing a successful vulnerability management program requires a strategic approach. Start by establishing clear goals and objectives tailored to your organization’s needs. This sets the foundation for effective prioritization.
Regularly schedule scans to identify vulnerabilities across systems, applications, and networks. Consistency is key; these assessments help catch emerging threats early.
Develop a risk-based remediation strategy. Not all vulnerabilities pose the same level of threat, so focus resources on addressing those that could lead to significant damage or data breaches.
Foster an environment of continuous improvement. Encourage feedback from team members and other stakeholders to refine processes over time.
Documentation plays a crucial role in maintaining transparency and accountability within the program. Regular reports can track progress while highlighting areas needing attention.
Invest in training for your team to stay updated on evolving security trends and tools. A knowledgeable team is better equipped to tackle challenges head-on.
ALSO READ: Everything About 2024 duolingo app review medium
Utilizing Automation in Vulnerability Management
Automation plays a pivotal role in modern vulnerability management. It streamlines processes, reducing the burden on team members and allowing them to focus on critical tasks.
By automating routine scans, organizations can quickly identify vulnerabilities across their systems. This rapid detection is vital for maintaining security posture.
Automated reporting tools also enhance visibility. They provide real-time insights into vulnerability status, enabling teams to prioritize remediation efforts effectively.
Integrating automation with existing workflows creates a seamless experience. Tools can be configured to trigger alerts or initiate patching without manual intervention.
Moreover, automation helps mitigate human error—a common pitfall in vulnerability management. By relying on technology for repetitive tasks, teams minimize risks associated with oversight or fatigue.
Leveraging automation empowers teams to respond swiftly and manage vulnerabilities more efficiently while continuously improving overall security measures.
The Importance of Communication and Collaboration within the Team
Effective communication is the backbone of any successful vulnerability management team. When team members share insights and updates, they create an environment ripe for proactive problem-solving.
Collaboration fosters a culture of trust. Team members are more likely to openly discuss vulnerabilities when they feel supported by their peers. This can lead to faster identification and remediation of risks.
Regular meetings can enhance synergy among diverse skill sets within the group. These sessions encourage brainstorming and collective decision-making, essential for tackling complex security challenges.
Utilizing collaborative tools adds further value. Platforms that allow real-time sharing of data help streamline processes and improve response times significantly.
Encouraging open dialogue about successes and setbacks also strengthens team dynamics. It creates learning opportunities that drive continuous improvement in your vulnerability management strategy.
ALSO READ: is medium a good platform for extracurricular activities
Measuring and Reporting on the Effectiveness of Your Vulnerability Management Strategy
Measuring the effectiveness of your vulnerability management strategy is crucial for continuous improvement. Start by defining key performance indicators (KPIs) that align with your organization’s goals. This could include metrics like time taken to remediate vulnerabilities or the percentage of critical issues resolved within a specific timeframe.
Regular reporting should be part of your routine. Share insights with stakeholders through dashboards and reports, emphasizing trends over time rather than just raw numbers. This approach helps highlight areas of success and those needing attention.
Engage team members in discussions about these metrics. Their input can provide valuable context to the data, revealing underlying challenges or successes not immediately visible through numbers alone.
Using an iterative process allows you to adapt and refine strategies based on what works best for your environment. Analyzing feedback regularly fosters a culture of transparency and accountability within the team, ensuring everyone stays aligned toward common security objectives.
Conclusion
Creating a road map for a vulnerability management team medium is crucial in today’s digital landscape. It serves as the backbone for safeguarding an organization against potential threats. By understanding the role of your team and outlining key responsibilities, you set yourself up for success.
Developing this road map requires thoughtful planning and execution. Adopting best practices ensures that your program not only addresses current vulnerabilities but also evolves with emerging threats. Utilizing automation can streamline processes, allowing your team to focus on strategic initiatives rather than manual tasks.
Communication and collaboration within the team enhance effectiveness, fostering an environment where ideas flow freely and challenges are met collectively. Measuring outcomes provides insights into what works well and what needs adjustment.
A well-structured vulnerability management strategy goes beyond just identifying weaknesses; it empowers organizations to take proactive measures against risks while maintaining operational integrity. As you implement these elements, you’ll create a robust defense mechanism that adapts seamlessly to the ever-changing cyber environment.
ALSO READ: Does Medium publish literature reviews? Key insights
FAQs
What is “road map for a vulnerability management team medium”?
A road map for a vulnerability management team medium outlines the strategies, roles, and steps for identifying and addressing cybersecurity risks, ensuring a proactive defense against evolving threats.
Why is a vulnerability management road map essential for cybersecurity?
It provides clear direction, helping teams prioritize vulnerabilities, allocate resources efficiently, and stay aligned with organizational security goals.
What are the key responsibilities of a vulnerability management team?
The team is responsible for identifying vulnerabilities, collaborating on remediation, monitoring fixes, reporting to stakeholders, and training employees on cybersecurity best practices.
How does automation aid in vulnerability management?
Automation streamlines routine scanning, reporting, and patching, enhancing speed, reducing human error, and enabling teams to focus on critical tasks for improved security posture.
How can communication improve vulnerability management outcomes?
Open communication fosters collaboration, accelerates risk identification, and ensures that teams are responsive, informed, and aligned in tackling security challenges effectively.
GENERAL
URLwo: Smarter Links That Humans and Search Engines Trust

In today’s digital landscape, where attention spans are fleeting and information overload is the norm, clarity and trust are paramount. Enter URLwo a game-changing link shortener designed to bridge the gap between human curiosity and search engine credibility. As we navigate a world filled with excessive data, having reliable tools at our fingertips can make all the difference. Whether you’re a business owner looking to enhance your online presence or an individual aiming for seamless sharing experiences, URLwo promises smarter links that resonate with both users and algorithms alike. Discover why URLwo rises above others in today’s dynamic link management landscape.
Inroduction to urlwo
URLwo emerged from the need for a smarter, more trustworthy way to share links online. It’s not just another link shortener; it redefines what users expect in terms of safety and reliability.
Unlike traditional URL shorteners, URLwo focuses on transparency. Users can easily see where their links lead before clicking, making it a breeze to avoid malicious sites or unwanted surprises. This trust is essential in an era when internet security is top of mind.
Moreover, URLwo integrates seamlessly with analytics tools, allowing businesses and individuals to track engagement effortlessly. Understanding how audiences interact with shared content becomes simpler than ever.
Designed for both casual users and professionals alike, URLwo makes link sharing efficient without sacrificing credibility. In a digital world often clouded by uncertainty, having a reliable tool like this can change your online experience dramatically.
The Evolution of URL Shorteners
The journey of URL shorteners began in the mid-2000s, driven by the need for brevity. As social media platforms emerged, character limits became a challenge. Long URLs cluttered posts and made sharing cumbersome.
Early solutions like TinyURL paved the way for this new trend. They offered simple functionality: take a lengthy link and shrink it down to size. This innovation was embraced widely, especially on Twitter.
As technology advanced, so did URL shorteners. New players entered the scene with added features such as analytics and customization options. Users craved not just shorter links but also insights into their performance.
Today’s landscape includes sophisticated tools that prioritize trustworthiness alongside convenience. With concerns over spam and phishing attacks rising, modern shorteners now focus on security while still delivering user-friendly experiences. The evolution continues as we look toward even smarter linking solutions.
Introducing URLwo: A Revolutionary Link Shortener
URLwo is not just another link shortener. It’s a game-changer in the world of digital marketing and online communication.
What sets URLwo apart? Its focus on building trust between users and search engines. Each shortened link created through URLwo carries an assurance of security, transparency, and reliability.
With advanced analytics features, users can track performance metrics like click rates and user engagement seamlessly. It gives companies the power to make strategic decisions with real-time intelligence.
Moreover, URLwo prioritizes user experience by offering customization options. You can create memorable links that resonate with your brand identity.
In a landscape flooded with generic URLs, URLwo stands out as a smart solution for individuals and companies alike. Embrace this revolutionary tool to enhance your online presence today!
How URLwo Works?
URLwo operates on a straightforward yet powerful mechanism. Users start by inputting their long URLs into the URLwo interface.
Once submitted, URLwo generates a shortened link that’s easy to share and remember. But it doesn’t stop there; each link is embedded with tracking capabilities.
This allows users to monitor clicks and engagement in real-time. The analytics dashboard provides insights on who clicked the link, where they are from, and what devices they used.
Security features are also built-in, ensuring every click is safe for both the user and their audience.
With customizable options available, businesses can brand their links while maintaining trustworthiness. This dual focus on functionality and security makes URLwo stand out in today’s crowded market of link shorteners.
Benefits of Using URLwo for Businesses and Individuals
URLwo offers a range of benefits tailored for both businesses and individuals. For companies, it enhances brand visibility through customizable links. This means every shortened URL can reflect your brand identity, making them memorable.
Individuals also gain from using URLwo by simplifying link sharing across social media and email platforms. A clean, concise link is more appealing to audiences.
Moreover, URLwo provides detailed analytics. Real-time tracking lets users see how audiences interact with their links. This data helps refine marketing strategies effectively.
Security is another critical advantage. With features that prioritize trustworthiness, users know they’re sharing safe links with their audience.
The user-friendly interface ensures that anyone can create a smart link quickly without technical expertise required. Whether you’re promoting content or enhancing communication channels, URLwo makes the process seamless and efficient.
User Testimonials
Users have been raving about URLwo since its launch. Many highlight the intuitive interface that makes link shortening a breeze.
“I’ve tried several services, but URLwo stands out for its reliability,” says Sarah, a digital marketer. She appreciates how seamlessly it integrates with her campaigns.
Another user, James, notes the transparency of analytics. “I can track engagement in real time, which helps me refine my strategies,” he explains.
Small business owner Emma loves the customization options available. “Being able to create branded links has enhanced my credibility online,” she shares excitedly.
These testimonials reflect a growing community that values not just functionality but trustworthiness in their link-shortening tools. User experiences underline how URLwo is transforming the way we share content on the web.
Comparison to Other Popular URL Shorteners
When comparing URLwo to other popular URL shorteners, a few key differences emerge. Many traditional services prioritize basic functionality over user experience. They often generate generic links that lack branding and trust.
URLwo stands out by offering customizable link options. Users can create branded links that reflect their identity or business, fostering trust among audiences. This feature is vital for businesses looking to maintain consistency in their messaging.
Another aspect is analytics. While some platforms provide limited tracking capabilities, URLwo delivers comprehensive insights about link performance. Marketers need data to refine strategies, and this tool provides just that.
Security also plays a crucial role in today’s digital landscape. Unlike many competitors, URLwo emphasizes secure links with advanced encryption features. This ensures users are protected from malicious activities while browsing through shortened URLs.
The combination of customization, robust analytics, and enhanced security makes URLwo a compelling choice against its rivals in the market.
Tips for Creating Trustworthy and Effective URLs
Creating trustworthy URLs is essential for user engagement and SEO. Start by using clear, descriptive keywords that reflect the content of the page. This helps both humans and search engines understand what to expect.
Keep it concise. Long URLs can look spammy or confusing, making users hesitant to click. Aim for simplicity while retaining meaning.
Incorporate your brand name into the URL if possible. This reinforces branding and builds trust with visitors who recognize your business.
Avoid special characters or unnecessary parameters that might complicate readability. Clean, straightforward links are easier to share and remember.
Consider utilizing HTTPS in your URL for added security. Users are more likely to trust a link that shows it’s safe from potential threats.
Regularly monitor your links’ performance as well. Analyzing data can guide improvements over time, ensuring they remain effective and relevant.
Conclusion
URLwo is paving the way for a new era in link management. As we’ve explored, it stands out among traditional URL shorteners by offering features that cater specifically to both human users and search engines. Its user-friendly interface, combined with powerful analytics and customization options, allows businesses and individuals alike to elevate their online presence.
The evolution of URL shorteners has brought us tools that are more than just space-savers; they are essential components of effective digital marketing strategies. With URLwo facilitating trust through transparency and branded links, users can feel confident about sharing information.
As you consider your own link-sharing practices, remember that creating trustworthy URLs goes beyond aesthetics—it’s about building credibility with your audience. By choosing a service like URLwo, you’re setting yourself up for success in an increasingly crowded digital landscape.
Whether you’re looking to enhance brand visibility or simply streamline your social media efforts, embracing smarter links could be the key to unlocking greater engagement and reach. The future looks promising for those who choose to innovate with tools like URLwo at their disposal.
GENERAL
Novcizpimkunot: Streamlining Workflows for Smarter Decisions

Introduction to Novcizpimkunot
In today’s rapidly evolving business landscape, efficiency reigns supreme. Companies are constantly searching for ways to enhance productivity and make smarter decisions. Enter novcizpimkunot a game changer in workflow management that’s designed to streamline processes and boost decision-making capabilities. This innovative approach takes the chaos out of daily operations, allowing teams to focus on what truly matters: growth and success. Whether you’re a small startup or a large corporation, understanding how novcizpimkunot can transform your workflows is crucial in today’s competitive landscape. Let’s dive into the incredible benefits it offers and explore how it can help elevate your organization to new heights.
The Benefits of Streamlining Workflows
Streamlining workflows brings clarity to complex processes. It simplifies tasks, making them easier to manage. When team members understand their roles and responsibilities, productivity naturally increases.
Eliminating bottlenecks is another advantage. By identifying inefficiencies, businesses can optimize their operations. This leads to faster project completion and improved customer satisfaction.
Cost savings follow closely behind. Reducing wasted time and resources directly impacts the bottom line. Businesses can channel those savings back into expansion and development efforts.
Enhanced communication is also a key benefit of streamlined workflows. Teams that collaborate effectively make informed decisions more swiftly. Information flows seamlessly, ensuring everyone stays on the same page.
Embracing streamlined systems fosters adaptability in a rapidly changing market environment. Organizations become more agile and responsive to new challenges or opportunities as they arise.
How Novcizpimkunot Can Help Improve Decision Making?
Novcizpimkunot revolutionizes the way businesses approach decision-making. By providing a streamlined workflow, it allows teams to access critical data quickly. This efficiency reduces delays and fosters timely decisions.
Its user-friendly interface allows users to effortlessly interpret complex data. Clear insights emerge from data that may have previously seemed overwhelming.
The platform also encourages collaboration among team members. Multiple stakeholders can contribute their perspectives, enhancing the overall quality of decisions made.
Moreover, Novcizpimkunot incorporates analytical tools that predict outcomes based on various scenarios. This feature empowers leaders to make informed choices rather than relying on instinct alone.
By integrating feedback loops within workflows, organizations can adapt strategies swiftly as new information arises. Embracing this adaptability ensures companies stay competitive in fast-paced markets.
Case Studies: Success Stories of Companies Using Novcizpimkunot
Several companies have transformed their operations by adopting novcizpimkunot. One notable example is a mid-sized manufacturing firm that faced persistent delays in project completion. By streamlining their workflows with novcizpimkunot, they reduced lead times by 30%. This dramatic improvement enabled them to meet customer demands more efficiently.
Another case involves a tech startup struggling with communication gaps among team members. After implementing novcizpimkunot, they saw enhanced collaboration and quicker decision-making processes. The result? A boost in product development speed and overall employee morale.
A healthcare provider also leveraged the power of novcizpimkunot to optimize patient scheduling systems. They experienced a significant decrease in appointment cancellations and increased patient satisfaction ratings as a direct outcome of improved workflow management.
These examples highlight the versatility of novcizpimkunot across various industries, showcasing its potential to facilitate smarter business decisions through streamlined operations.
Steps to Implementing Novcizpimkunot in Your Business
Implementing novcizpimkunot in your business begins with a clear understanding of your current workflows. Identify key areas that require improvement and gather input from team members for insights.
Next, choose the right tools or software that align with the novcizpimkunot methodology. These resources will help facilitate smoother transitions and enhance communication.
Training is crucial. Ensure all employees understand how to use new systems effectively. Consider workshops or hands-on sessions to build confidence.
After implementation, monitor progress closely. Use metrics to evaluate efficiency gains and make adjustments as needed.
Encourage open feedback from your team throughout this process. Their experiences can uncover unforeseen challenges and opportunities for further optimization.
Common Challenges and Solutions for Implementing Workflow Streamlining Systems
Implementing workflow streamlining systems like novcizpimkunot can present several challenges. Resistance to change is often at the forefront. Employees may be accustomed to their established routines, making it tough to embrace new processes.
Another common hurdle is inadequate training. Without proper guidance, teams might struggle with adopting the system effectively. Investing in comprehensive training sessions can significantly ease this transition.
Integration issues frequently arise when existing tools are not compatible with new software. Conducting thorough compatibility checks beforehand mitigates this risk.
Data overload can overwhelm users if information isn’t organized clearly within the system. Establishing clear guidelines for data entry and management ensures a smoother experience and enhances decision-making efficiency as intended by novcizpimkunot.
Conclusion
Streamlining workflows has become essential for businesses aiming to enhance efficiency and make smarter decisions. Novcizpimkunot stands out as a powerful tool that empowers organizations to refine their processes, leading to significant improvements in decision-making.
By adopting Novcizpimkunot, companies can experience streamlined operations, reduced redundancy, and enhanced collaboration among teams. The case studies highlight real-world success stories where organizations have seen measurable results after implementing this system.
However, understanding potential challenges during implementation is crucial for a smooth transition. By addressing these obstacles with proactive strategies, businesses can fully leverage the benefits of workflow streamlining.
Embracing novcizpimkunot could be the key to unlocking new levels of productivity and insight within your organization. Take the leap towards smarter decisions today!
GENERAL
Wapbald: The New Digital Language Powering Innovation

Introduction to Wapbald and its origins
In a world where digital communication evolves at lightning speed, a new player has emerged on the scene: Wapbald. This innovative language isn’t just another tool; it’s transforming how we connect and share ideas in our increasingly digital lives. Born from the necessity for efficiency and clarity, Wapbald is carving out its niche as the go-to language for tech-savvy individuals and businesses alike. But what exactly sets it apart? Join us as we explore the origins of Wapbald, its unique features, and how it’s paving the way for revolutionary changes across various industries. Whether you’re a curious learner or a seasoned professional looking to stay ahead of the curve, understanding Wapbald could open doors you never knew existed.
How Wapbald is revolutionizing communication in the digital age?
Wapbald is transforming how we communicate in our fast-paced digital world. This innovative language bridges gaps that traditional languages often overlook.
By using concise syntax and dynamic symbols, Wapbald enhances clarity and reduces misunderstandings. It’s particularly effective in environments where quick exchanges are crucial, such as tech development or customer service.
Visual elements play a significant role too—integrating emojis and icons allows users to convey emotions effortlessly. This multimedia approach resonates especially with younger generations who thrive on visual communication.
Moreover, Wapbald’s adaptability across platforms makes it ideal for social media interactions, video games, and collaborative projects. As businesses increasingly rely on global teams, having a universal language like Wapbald fosters inclusivity among diverse cultures.
This revolution isn’t just about speed; it’s about enhancing connection in an era dominated by technology-driven interactions.
The unique features of Wapbald and how it differs from other digital languages
Wapbald stands out among digital languages with its innovative syntax and structure. Unlike traditional programming languages, it emphasizes brevity and clarity, allowing users to convey complex ideas in fewer lines of code.
One unique feature is its intuitive visual interface. This makes coding more accessible for beginners while still offering depth for seasoned developers. The drag-and-drop functionality simplifies the learning curve significantly.
Additionally, Wapbald incorporates natural language processing capabilities. Users can write commands that resemble conversational phrases, making it easier to understand and implement instructions without extensive technical jargon.
Another notable aspect is its adaptability across various platforms. Whether it’s web development or mobile applications, Wapbald’s versatility allows seamless integration into different environments.
These attributes position Wapbald as a revolutionary tool in digital communication that fosters collaboration and innovation like never before.
Real-life applications of Wapbald in various industries
Wapbald is making waves across multiple industries, transforming the way we interact with technology and each other. In healthcare, its concise syntax allows for quick communication between doctors and patients, streamlining processes that can often be bogged down by jargon.
In the tech sector, Wapbald simplifies coding languages. Developers find it easier to collaborate on projects using its intuitive structure. This not only boosts productivity but also encourages creativity in problem-solving.
Education is another field where Wapbald shines. Teachers are integrating it into their curricula to prepare students for a digital future. Its engaging format makes learning fun and accessible.
Even marketing teams benefit from this new language. Crafting compelling messages becomes more effective when using Wapbald’s unique features tailored for engagement and clarity. The adaptability of Wapbald ensures it meets diverse needs across various sectors seamlessly.
The benefits of learning Wapbald and its potential for career advancement
Learning Wapbald opens up a multitude of career opportunities in today’s tech-driven world. This digital language is becoming increasingly vital in various sectors, from marketing to software development.
Professionals who grasp Wapbald can enhance their communication skills, making collaboration smoother and more efficient. Being fluent in this innovative language sets individuals apart in job interviews and promotions.
Additionally, companies are actively seeking talent proficient in Wapbald for roles that require modern problem-solving techniques. As businesses embrace technological advancements, understanding this digital dialect positions you as an asset.
Moreover, learning Wapbald encourages creativity and adaptability. These qualities are essential for thriving in any industry where innovation is key.
By mastering Wapbald, you’re not just acquiring a new skill; you’re paving the way to exciting prospects that could shape your professional journey significantly.
How to get started with learning Wapbald?
Getting started with Wapbald is easier than you might think. First, immerse yourself in the basics by exploring online resources. Websites dedicated to digital languages often feature introductory guides specific to Wapbald.
Next, consider joining community forums or social media groups focused on Wapbald. Engaging with others can provide real-time support and insights from experienced users.
Practice regularly using interactive tools and applications designed for learning Wapbald. These platforms often include exercises that reinforce your understanding of syntax and semantics.
Additionally, look for webinars or workshops hosted by experts in the field. Live instruction can give you a deeper appreciation of its nuances.
Don’t forget about collaboration! Partnering with fellow learners can enhance your skills through shared knowledge and peer feedback. Embrace this innovative language journey as an exciting opportunity for growth!
Future developments and possibilities for Wapbald
Wapbald is just starting to scratch the surface of its potential. As more people adopt this innovative digital language, we can expect exciting advancements on the horizon.
One possibility lies in integration with AI technologies. Imagine a future where Wapbald algorithms enhance natural language processing, making communication even smoother and more intuitive.
The expansion into educational platforms is another avenue worth exploring. Learning Wapbald could become essential in tech curricula around the world, preparing students for careers in emerging fields.
As industries evolve, so will Wapbald’s applications. From real-time translation services to interactive virtual environments, its versatility may soon be unmatched.
Furthermore, community-driven content creation can fuel rapid growth and adaptability of this language. Users collaborating globally might lead to new dialects or variations that cater to specific needs or cultures.
With innovation at its core, Wapbald’s promises an exhilarating journey ahead.
Conclusion
Wapbald’s represents a significant leap in the way we communicate and innovate in our digital world. Its unique structure and dynamic features set it apart from existing languages, making it an essential tool for various industries. The real-life applications of Wapbald’s are expanding rapidly, showcasing its versatility and potential to streamline processes.
As more professionals recognize the benefits of learning Wapbald’s, career advancement opportunities will likely increase. By embracing this new language, individuals can position themselves at the forefront of technological innovation.
Getting started with Wapbald’s is easier than ever thanks to numerous online resources and communities dedicated to its growth. As interest continues to surge, future developments hold promise for further integrating Wapbald’s into everyday communication.
The journey with Wapbald’s is just beginning. Engaging with this digital language could open doors you never knew existed while shaping how we interact in our increasingly connected world.

 HOME IMPROVEMENT11 months ago
HOME IMPROVEMENT11 months agoThe Do’s and Don’ts of Renting Rubbish Bins for Your Next Renovation

 BUSINESS12 months ago
BUSINESS12 months agoExploring the Benefits of Commercial Printing

 BUSINESS12 months ago
BUSINESS12 months agoBrand Visibility with Imprint Now and Custom Poly Mailers

 HEALTH7 months ago
HEALTH7 months agoThe Surprising Benefits of Weight Loss Peptides You Need to Know

 HEALTH7 months ago
HEALTH7 months agoYour Guide to Shedding Pounds in the Digital Age

 TECHNOLOGY10 months ago
TECHNOLOGY10 months agoDizipal 608: The Tech Revolution Redefined

 HOME IMPROVEMENT7 months ago
HOME IMPROVEMENT7 months agoGet Your Grout to Gleam With These Easy-To-Follow Tips

 HEALTH11 months ago
HEALTH11 months agoHappy Hippo Kratom Reviews: Read Before You Buy!












