GENERAL
road map for a vulnerability management team medium
Introduction to road map for a vulnerability management team medium
In today’s digital landscape, the importance of a robust vulnerability management team cannot be overstated. As cyber threats evolve and become more sophisticated, organizations must stay one step ahead to safeguard their assets. A well-structured road map for a vulnerability management team medium provides that crucial direction. It lays out clear strategies, responsibilities, and best practices to navigate the complexities of identifying and mitigating vulnerabilities effectively.
Imagine having a detailed plan in place that not only addresses current weaknesses but also anticipates future challenges. This blog post will explore how to develop an effective road map tailored specifically for your team’s needs while enhancing collaboration and communication along the way. Join us as we delve into the key components essential for building an exceptional vulnerability management program that stands resilient against ever-changing threats!
ALSO READ: Predovac: Innovating the Education Landscape
Understanding the Role of road map for a vulnerability management team medium
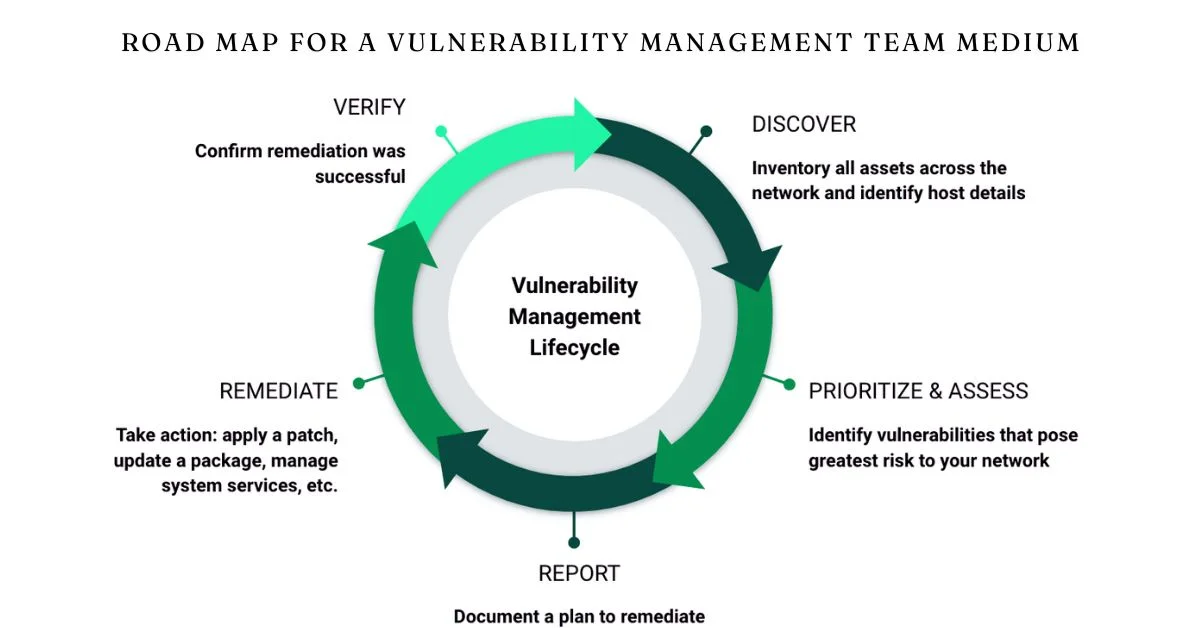
A well-defined road map for a vulnerability management team medium acts as both a guide and blueprint. It outlines the strategic direction, ensuring everyone understands their roles and responsibilities.
The role of this road map is multifaceted. First, it prioritizes vulnerabilities based on risk levels, allowing teams to focus on what matters most.
This approach helps in resource allocation—ensuring that time and effort target the highest risks rather than spreading resources too thinly across less critical issues.
Moreover, it fosters alignment within the team by setting clear objectives and timelines. This clarity enhances accountability among members while reducing redundancy.
Having a structured plan aids in adapting to new threats or changes within an organization’s infrastructure swiftly. A responsive strategy keeps security measures relevant amidst evolving cyber landscapes.
Key Responsibilities of a Vulnerability Management Team
A vulnerability management team plays a crucial role in safeguarding an organization’s assets. Their first responsibility is to identify vulnerabilities across all systems. This involves continuous scanning, assessing risks, and prioritizing issues based on potential impact.
Next comes remediation. The team collaborates with IT departments to ensure that identified vulnerabilities are addressed swiftly and effectively. They provide guidance on patch management and system updates.
Monitoring is another key task. After remediation, the team must analyze whether fixes have been successful or if further action is necessary.
Reporting also falls under their purview. Regular updates for stakeholders keep everyone informed of the current security posture and any emerging threats.
Training employees about best practices in cybersecurity rounds out their responsibilities, fostering a culture of security awareness throughout the organization.
ALSO READ: Everything about pinterest engineering blog experiments
Developing a road map for a vulnerability management team medium
Creating a road map for a vulnerability management team requires careful planning and strategic thinking. Start by defining the team’s goals. Prioritize what needs immediate attention versus what can be addressed later.
Next, assess your current vulnerabilities and resources. This assessment will inform your team’s capacity to tackle threats effectively. Identify tools that support automation and streamline processes.
Establish clear timelines for each phase of the plan. Short-term milestones build momentum, while long-term objectives keep everyone focused on broader targets.
Involve key stakeholders early in the process to ensure alignment across departments. Regular feedback loops are essential for adapting strategies as new threats emerge or organizational priorities shift.
Document every step taken along this journey. A transparent record not only tracks progress but also helps refine future initiatives.
Best Practices for Implementing and Maintaining a Successful Vulnerability Management Program
Implementing a successful vulnerability management program requires a strategic approach. Start by establishing clear goals and objectives tailored to your organization’s needs. This sets the foundation for effective prioritization.
Regularly schedule scans to identify vulnerabilities across systems, applications, and networks. Consistency is key; these assessments help catch emerging threats early.
Develop a risk-based remediation strategy. Not all vulnerabilities pose the same level of threat, so focus resources on addressing those that could lead to significant damage or data breaches.
Foster an environment of continuous improvement. Encourage feedback from team members and other stakeholders to refine processes over time.
Documentation plays a crucial role in maintaining transparency and accountability within the program. Regular reports can track progress while highlighting areas needing attention.
Invest in training for your team to stay updated on evolving security trends and tools. A knowledgeable team is better equipped to tackle challenges head-on.
ALSO READ: Everything About 2024 duolingo app review medium
Utilizing Automation in Vulnerability Management
Automation plays a pivotal role in modern vulnerability management. It streamlines processes, reducing the burden on team members and allowing them to focus on critical tasks.
By automating routine scans, organizations can quickly identify vulnerabilities across their systems. This rapid detection is vital for maintaining security posture.
Automated reporting tools also enhance visibility. They provide real-time insights into vulnerability status, enabling teams to prioritize remediation efforts effectively.
Integrating automation with existing workflows creates a seamless experience. Tools can be configured to trigger alerts or initiate patching without manual intervention.
Moreover, automation helps mitigate human error—a common pitfall in vulnerability management. By relying on technology for repetitive tasks, teams minimize risks associated with oversight or fatigue.
Leveraging automation empowers teams to respond swiftly and manage vulnerabilities more efficiently while continuously improving overall security measures.
The Importance of Communication and Collaboration within the Team
Effective communication is the backbone of any successful vulnerability management team. When team members share insights and updates, they create an environment ripe for proactive problem-solving.
Collaboration fosters a culture of trust. Team members are more likely to openly discuss vulnerabilities when they feel supported by their peers. This can lead to faster identification and remediation of risks.
Regular meetings can enhance synergy among diverse skill sets within the group. These sessions encourage brainstorming and collective decision-making, essential for tackling complex security challenges.
Utilizing collaborative tools adds further value. Platforms that allow real-time sharing of data help streamline processes and improve response times significantly.
Encouraging open dialogue about successes and setbacks also strengthens team dynamics. It creates learning opportunities that drive continuous improvement in your vulnerability management strategy.
ALSO READ: is medium a good platform for extracurricular activities
Measuring and Reporting on the Effectiveness of Your Vulnerability Management Strategy
Measuring the effectiveness of your vulnerability management strategy is crucial for continuous improvement. Start by defining key performance indicators (KPIs) that align with your organization’s goals. This could include metrics like time taken to remediate vulnerabilities or the percentage of critical issues resolved within a specific timeframe.
Regular reporting should be part of your routine. Share insights with stakeholders through dashboards and reports, emphasizing trends over time rather than just raw numbers. This approach helps highlight areas of success and those needing attention.
Engage team members in discussions about these metrics. Their input can provide valuable context to the data, revealing underlying challenges or successes not immediately visible through numbers alone.
Using an iterative process allows you to adapt and refine strategies based on what works best for your environment. Analyzing feedback regularly fosters a culture of transparency and accountability within the team, ensuring everyone stays aligned toward common security objectives.
Conclusion
Creating a road map for a vulnerability management team medium is crucial in today’s digital landscape. It serves as the backbone for safeguarding an organization against potential threats. By understanding the role of your team and outlining key responsibilities, you set yourself up for success.
Developing this road map requires thoughtful planning and execution. Adopting best practices ensures that your program not only addresses current vulnerabilities but also evolves with emerging threats. Utilizing automation can streamline processes, allowing your team to focus on strategic initiatives rather than manual tasks.
Communication and collaboration within the team enhance effectiveness, fostering an environment where ideas flow freely and challenges are met collectively. Measuring outcomes provides insights into what works well and what needs adjustment.
A well-structured vulnerability management strategy goes beyond just identifying weaknesses; it empowers organizations to take proactive measures against risks while maintaining operational integrity. As you implement these elements, you’ll create a robust defense mechanism that adapts seamlessly to the ever-changing cyber environment.
ALSO READ: Does Medium publish literature reviews? Key insights
FAQs
What is “road map for a vulnerability management team medium”?
A road map for a vulnerability management team medium outlines the strategies, roles, and steps for identifying and addressing cybersecurity risks, ensuring a proactive defense against evolving threats.
Why is a vulnerability management road map essential for cybersecurity?
It provides clear direction, helping teams prioritize vulnerabilities, allocate resources efficiently, and stay aligned with organizational security goals.
What are the key responsibilities of a vulnerability management team?
The team is responsible for identifying vulnerabilities, collaborating on remediation, monitoring fixes, reporting to stakeholders, and training employees on cybersecurity best practices.
How does automation aid in vulnerability management?
Automation streamlines routine scanning, reporting, and patching, enhancing speed, reducing human error, and enabling teams to focus on critical tasks for improved security posture.
How can communication improve vulnerability management outcomes?
Open communication fosters collaboration, accelerates risk identification, and ensures that teams are responsive, informed, and aligned in tackling security challenges effectively.
GENERAL
Understanding Crypto Casinos: A Beginner’s Guide

In recent years, the rise of cryptocurrency has brought about a new era in online gambling with the emergence of crypto casinos. These innovative platforms offer players the opportunity to gamble with digital currencies like Bitcoin, Ethereum, and Litecoin, revolutionizing the way we experience online gaming. In this beginner’s guide, we’ll delve into what crypto casinos are, how they work, the benefits of using cryptocurrency for gambling, and provide step-by-step instructions on how to get started. Plus, we’ll share valuable tips for choosing a reputable crypto casino.
What are Crypto Casinos?
Crypto casinos are online gambling platforms that accept cryptocurrency as a form of payment. Unlike traditional online casinos that typically rely on fiat currencies like USD, EUR, or GBP, crypto casinos exclusively transact in digital currencies. These platforms leverage blockchain technology to facilitate secure and transparent transactions, ensuring fairness and anonymity for players.
Benefits of Using Cryptocurrency for Gambling
There are several benefits to using cryptocurrency for gambling at crypto casinos. Firstly, transactions are fast and secure, with deposits and withdrawals processed almost instantly. Additionally, cryptocurrency transactions are typically anonymous, providing a level of privacy that is not always possible with traditional payment methods. Moreover, using cryptocurrency eliminates the need for third-party payment processors, reducing the risk of fraud and lowering transaction fees.
Getting Started with Crypto Gambling
Getting started with crypto gambling is straightforward, even for beginners. Here’s a step-by-step guide to help you begin your journey:
- Choose a Cryptocurrency Wallet: Start by selecting a reputable cryptocurrency wallet to store your digital assets securely. Popular options include hardware wallets like Ledger Nano S or software wallets like Trust Wallet and MetaMask.
- Acquire Cryptocurrency: Next, acquire the cryptocurrency of your choice by purchasing it from a reputable exchange or through peer-to-peer transactions. Ensure that you choose a reliable exchange platform with robust security measures in place.
- Select a Crypto Casino: Research and choose a reputable crypto casino that meets your gaming preferences and offers a wide range of games. Look for factors such as licensing, game variety, bonuses and promotions, customer support, and user reviews.
- Register an Account: Once you’ve selected a crypto casino, register an account by providing your basic information and creating a username and password.
- Deposit Cryptocurrency: Navigate to the casino’s deposit section and select your preferred cryptocurrency. Follow the on-screen instructions to generate a deposit address and transfer your funds from your wallet to the casino.
- Start Playing: With your funds deposited, you’re ready to start playing your favourite casino games. Explore the diverse range of games available, including slots, blackjack, roulette, poker, and more.
Tips for Choosing a Reputable Crypto Casino
When choosing a crypto casino, it’s essential to consider several factors to ensure a safe and enjoyable gaming experience:
- Licensing and Regulation: Look for casinos that are licensed and regulated by reputable gaming authorities, ensuring fairness and compliance with industry standards.
- Game Variety: Opt for casinos that offer a diverse range of games from leading software providers, ensuring high-quality gameplay and entertainment options.
- Security Measures: Check for robust security measures such as SSL encryption, two-factor authentication, and provably fair gaming to protect your personal and financial information.
- Bonuses and Promotions: Choose casinos that offer generous bonuses and promotions, including welcome bonuses, free spins, and loyalty rewards, to maximise your gaming experience.
- Customer Support: Select casinos with responsive and helpful customer support available 24/7 via live chat, email, or phone to assist you with any queries or issues.
By following these tips and guidelines, you can confidently choose a reputable crypto casino and embark on an exciting journey into the world of crypto gambling. With its myriad benefits and the convenience of digital currency, crypto casinos offer a unique and immersive gaming experience that is sure to captivate players worldwide. So why wait? Join the crypto gambling revolution today and experience the thrill of Dapp Casino and other leading platforms in the crypto gambling space.
GENERAL
What Is Stimulus Control: Breaking the Cycle of Nail Biting

Nail biting is a common habit that many find hard to break. But have you heard of stimulus control?
This blog explores what is stimulus control and how it can help in overcoming nail biting. Stimulus control is a behavior modification technique aimed at recognizing and altering the stimuli that trigger unwanted habits.
By understanding this concept, individuals can learn to interrupt the cycle of nail biting. Whether it’s stress, boredom, or anxiety, stimulus control offers a way out. Join us as we uncover the secrets to breaking free from the cycle of nail biting.
Understanding Nail Biting
Biting your nails is more than just a bad habit; it’s a response to many mental and environmental factors. The things that can make someone bite their nails are stress, anxiety, boredom, and not being able to focus. The first step to breaking a habit is to figure out what makes it happen.
The Basics of Stimulus Control
Finding and changing the things that cause a certain behavior is what stimulus control is all about. For people who bite their nails, this could mean figuring out what situations or feelings make them more likely to do it and then changing those things to stop the behavior.
Identifying Your Triggers
The key to effective stimulus control is accurately identifying your triggers. Common triggers for nail biting include stress, anxiety, boredom, or engaging in stress management techniques and activities that allow the hands to be free, such as watching TV. Keeping a journal can help pinpoint when and why you bite your nails.
Changing Your Environment
Once you’ve identified your triggers, the next step is to change your environment to make nail biting less likely. This could involve keeping your hands busy, such as by holding a stress ball or engaging in activities that require both hands.
Implementing Barriers to Nail Biting
Putting up physical barriers can also help stop people from biting their nails. Putting tape over your nails, gloves on, or bitter-tasting nail polish on them can make biting less appealing or harder to do.
The Role of Replacement Behaviors
Finding a healthy behavior modification is crucial for breaking the habit. This could be as simple as squeezing a stress ball or fiddling with a rubber band when you feel the urge to bite your nails. Replacement behaviors provide an alternative way to cope with behavioral triggers.
Seeking Professional Help
Sometimes, breaking the cycle of nail-biting requires more than just self-help strategies. Cognitive-behavioral therapy (CBT) and other forms of psychological counseling can be highly effective in addressing the root causes of nail biting.
Maintaining Progress
Breaking any habit requires time and patience. Celebrate your successes, and if you relapse, don’t be too hard on yourself.
Understanding what led to the relapse can help you strengthen your strategy moving forward. For more detailed guidance on identifying triggers and implementing effective strategies, read more articles on how to stop biting your nails.
Understanding What Is Stimulus Control and Its Effect on Your Life
You can stop biting your nails if you know what is stimulus control and how to control it. Figuring out what makes people do bad things and changing those things can help them stop.
Setting up trigger responses with control over stimuli is structured. Habits can be broken by making changes to the environment, putting up barriers, and finding new things to do.
When you control your stimuli, you can stop biting your nails and feel better in general. These methods can help people behave better over time.
Did you like this guide? Great! Please browse our website for more!
GENERAL
Unique Ideas for Cheap Funeral Flower Arrangements

Having trouble figuring out how to plan a polite and emotional goodbye on a tight budget? You’re not by yourself. Welcome to our guide on Ideas for Cheap Funeral Flower Arrangements. These arrangements will help you add a bit of class and comfort without spending a lot of money.
Expressing sympathy and remembering a loved one’s life doesn’t have to cost a lot of money, they say. Come with us as we talk about creative and inexpensive ways to honor the life of a loved one with flowers that say a lot about love and remembering them.
Single Stem Tributes
Instead of big, complicated designs, you could use single stems of the person’s favorite flower in small boxes or jars. This can save you money and make a show that is both simple and powerful.
These minimalist arrangements not only show off the elegance of simplicity but also convey a message with fewer components. Because they can make you feel calm and remember things clearly, they are great for people who want to show strong feelings in a subtle way.
Potted Plants
Use potted plants as funeral flower arrangements so that people can take home a live memory of your loved one. Not only are succulents and small herbs cheap, but they are also a permanent remembrance that can be cared for and loved for many years.
Choosing growing plants as sympathy flowers is good for the environment and will last for a long time as a reminder of growth and renewal during this hard time. This way of doing things not only honors the memory of the dead but also shows comforting support and concern.
Personalized Bouquets
Use the person’s favorite flowers or colors to make a bouquet, and add personal touches like pictures, small items, or handmade notes. You can use this as a beautiful memory that shows how unique your loved one is.
DIY funeral flowers are an important way to show your grief while also keeping costs low for people who like to add a more personal touch. This method lets families work together to create unique honors, which strengthens relationships through shared memories and imagination.
Flower Alternatives
If you want something a little different, you could use things that aren’t flowers, like feathers, seashells, or even tree twigs and leaves. The funeral preparations can be made more special and unique this way, and it won’t cost much either.
Utilizing these creative suggestions for picking flowers for funeral arrangements not only helps you stick to your budget but also gives the ceremony a very personal touch. Keep in mind that the care and love that goes into selecting or making flowers for funeral gifts is worth much more than the money they cost.
Affordable Elegance: Final Touches with Cheap Funeral Flower Arrangements
To say goodbye to a loved one in a meaningful way doesn’t have to cost a lot of money. With these unique ideas for cheap funeral flower arrangements, you can honor their memory in a beautiful and classy way without spending a lot of money.
Don’t forget that the thought and love that went into the memorial are more important than the price. Let your imagination and unique style show in every flower arrangement you make, and let them be a sign of love and memory for years to come.
Did you find this article helpful? Explore our site for more informational and entertaining articles that could guide you!

 TECHNOLOGY4 months ago
TECHNOLOGY4 months agoBlog Arcy Art: Where Architecture Meets Art

 ENTERTAINMENT6 days ago
ENTERTAINMENT6 days agoExploring the Kristen Archives: A Treasure Trove of Erotica and More

 ENTERTAINMENT2 days ago
ENTERTAINMENT2 days agoKiss KH: The Streaming Platform Redefining Digital Engagement and Cultural Currents

 LIFESTYLE4 months ago
LIFESTYLE4 months agoThe Disciplinary Wives Club: Spanking for Love, Not Punishment

 LIFESTYLE6 days ago
LIFESTYLE6 days agoWho Is Sandra Orlow?

 EDUCATION2 days ago
EDUCATION2 days agoLingrohub Platform: A Complete Student Access Guide

 ENTERTAINMENT3 weeks ago
ENTERTAINMENT3 weeks agoMonkeyGG2: Your Personal Gaming Hub

 TECHNOLOGY2 days ago
TECHNOLOGY2 days agoCasibom: The Digital Alchemy Reshaping Systems, Society, and Self