BUSINESS
Demystifying Logic Gates: The Building Blocks of Digital Circuits
Introduction
Logic gates are basic parts in the domain of computerized gadgets. They are the structure obstructs that structure the underpinning of computerized circuits, empowering the production of complicated computational frameworks. This article plans to demystify rationale doors, investigating their sorts, capabilities, and applications, and giving a thorough manual for anyone with any interest in the field of computerized hardware.
What Are Logic Gates?
Logic gates are electronic gadgets that carry out essential consistent roles in view of at least one parallel data sources, creating a solitary paired yield. These doors work on the standards of Boolean variable based math and are fundamental in planning computerized circuits. By manipulating binary signals, logic gates enable devices to perform tasks ranging from simple arithmetic to complex decision-making processes.
Types of Logic Gates
There are a few fundamental kinds of rationale doors, each with an extraordinary capability and image. Here, we’ll investigate the most widely recognized ones:
AND Gate
- Symbol and Truth Table: The AND door yields a high sign (1) provided that every one of its bits of feedbacks are high. Its image is a D-molded figure with numerous information sources meeting into a solitary result. Reality table for a two-information AND door is as per the following:
| A | B | Output |
|---|---|---|
| 0 | 0 | 0 |
| 0 | 1 | 0 |
| 1 | 0 | 0 |
| 1 | 1 | 1 |
- Practical Applications: Used in situations where multiple conditions must be met simultaneously, such as in safety systems and control mechanisms.
OR Gate
- Symbol and Truth Table: The OR gate outputs a high signal if at least one input is high. Its symbol is a curved line converging into a single output. The truth table is:
| A | B | Output |
|---|---|---|
| 0 | 0 | 0 |
| 0 | 1 | 1 |
| 1 | 0 | 1 |
| 1 | 1 | 1 |
- Practical Applications: Common in circuits where multiple paths can lead to a single outcome, like in lighting systems.
NOT Gate
- Symbol and Truth Table: The NOT gate, or inverter, outputs the opposite of the input signal. Its symbol is a triangle with a small circle at the output. The truth table is:
| A | Output |
|---|---|
| 0 | 1 |
| 1 | 0 |
- Practical Applications: Used to invert signals, essential in binary operations and computing.
NAND Gate
- Symbol and Truth Table: The NAND gate outputs a low signal only if all inputs are high. Its symbol is similar to the AND gate but with a small circle at the output. The truth table is:
| A | B | Output |
|---|---|---|
| 0 | 0 | 1 |
| 0 | 1 | 1 |
| 1 | 0 | 1 |
| 1 | 1 | 0 |
- Practical Applications: Widely used in digital logic circuits due to its ability to create any other logic gate when combined appropriately.
NOR Gate
- Symbol and Truth Table: The NOR gate outputs a high signal only if all inputs are low. Its symbol is similar to the OR gate but with a small circle at the output. The truth table is:
| A | B | Output |
|---|---|---|
| 0 | 0 | 1 |
| 0 | 1 | 0 |
| 1 | 0 | 0 |
| 1 | 1 | 0 |
- Practical Applications: Used in digital logic circuits to perform logical NOR operations.
XOR Gate
- Symbol and Truth Table: The XOR (exclusive OR) door yields a high sign if by some stroke of good luck one of the sources of info is high. Its symbol is an OR gate with an additional curved line. The truth table is:
| A | B | Output |
|---|---|---|
| 0 | 0 | 0 |
| 0 | 1 | 1 |
| 1 | 0 | 1 |
| 1 | 1 | 0 |
- Practical Applications: Used in circuits where exclusive conditions are required, such as in error detection and correction systems.
XNOR Gate
- Symbol and Truth Table: The XNOR (exclusive NOR) door yields a high sign in the event that the data sources are equivalent. Its image is a XOR entryway with a little circle at the result. The truth table is:
| A | B | Output |
|---|---|---|
| 0 | 0 | 1 |
| 0 | 1 | 0 |
| 1 | 0 | 0 |
| 1 | 1 | 1 |
- Practical Applications: Used in parity checkers and digital comparators.
Combinational Logic Circuits
Combinational logic circuits comprise of rationale doors whose results are resolved exclusively by the ongoing data sources. Models incorporate adders, multiplexers, and encoders.
Sequential Logic Circuits
Dissimilar to combinational circuits, consecutive rationale circuits have yields that rely upon both current and past sources of info, consolidating memory components. Models incorporate flip-slumps, counters, and shift registers. These circuits are essential for tasks requiring storage and timing, such as in clocks and memory units.
Boolean Algebra and Logic Gates
Boolean variable based math gives the numerical system to examining and planning rationale circuits. Boolean articulations address the connections among information sources and results of rationale doors. For instance, the articulation A·B addresses an AND operation, while A + B addresses an OR operation. Understanding Boolean variable based math is critical to rearranging and streamlining advanced circuits.
Truth Tables
Truth tables list all conceivable information blends and their relating yields for a rationale door. They are important instruments for understanding and planning rationale circuits. For each kind of door, reality table layouts the normal way of behaving, filling in as a source of perspective for circuit creators.
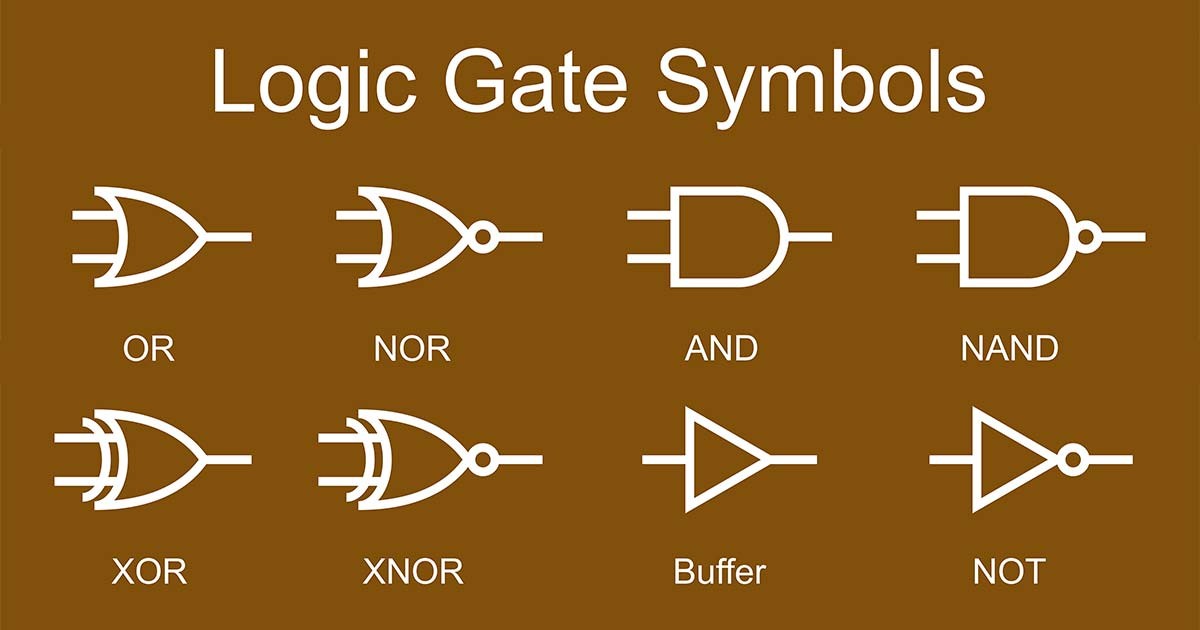
Logic Gate Symbols
Standard symbols are used in circuit diagrams to represent different logic gates. The American and international symbols differ slightly but convey the same functions. Familiarity with these symbols is essential for reading and creating circuit diagrams.
Practical Applications of Logic Gates
Logic gates are pervasive in present day innovation. They are tracked down in PCs, cell phones, and different other electronic gadgets. From basic dynamic cycles to complex computational undertakings, rationale doors are indispensable to the usefulness of advanced frameworks.
Building Complex Circuits with Logic Gates
By consolidating numerous rationale doors, complex circuits can be worked to perform modern activities. Models incorporate arithmetic logic units (ALUs) in processors and digital signal processing(DSP) circuits. Understanding how to consolidate entryways actually is critical for cutting edge advanced plan.
Integrated Circuits and Logic Gates
Integrated circuits (ICs) integrate various rationale doors into a solitary chip, improving execution and diminishing size. ICs are the foundation of present day hardware, empowering the making of minimized and strong gadgets. Rationale doors inside ICs play out various capabilities, from essential rationale activities to complex information handling.
Digital vs. Analog Circuits
Digital circuits utilize discrete voltage levels to address paired information, while simple circuits utilize constant voltage levels. Logic gates are principal to digital circuits, empowering exact control and control of parallel signs. Understanding the distinctions among computerized and simple circuits helps in choosing the fitting innovation for a given application.
Simulation and Testing of Logic Circuits
Simulation tools and programming, like SPICE and Verilog, permit fashioners to test and check rationale circuits before actual execution. Testing guarantees that circuits proceed true to form and distinguishes and right issues from the get-go in the plan cycle.
Challenges in Logic Gate Design
Designing rationale doors includes defeating different difficulties, including power utilization, speed, and commotion insusceptibility. Progressions in semiconductor innovation keep on tending to these difficulties, pushing the limits of what is conceivable in digital electronics.
Learning and Experimenting with Logic Gates
Instructive assets, like reading material, online courses, and intuitive reenactments, give important learning valuable open doors to those keen on rationale entryways. Do-It-Yourself activities and packs offer involved insight, assisting fans with applying hypothetical information to commonsense applications.
Conclusion
Logic gates are the central structure blocks of advanced circuits, supporting the usefulness of endless electronic gadgets. Grasping their sorts, capabilities, and applications is fundamental for anyone with any interest at all in computerized hardware. By demystifying rationale entryways, we gain a more profound enthusiasm for the innovation that drives our computerized world.
FAQs
- What are the most fundamental logic gates?
- The most basic logic gates are AND, OR, and NOT gates.
- How do logic gates affect computer performance?
- Logic gates perform the basic operations that enable computational processes, directly impacting the speed and efficiency of a computer.
- Could rationale doors be utilized in analog circuits?
- Logic gates are essentially utilized in advanced circuits, however they can connect with simple circuits in contradicting message plans.
- What is the contrast between a logic gates and a transistor?
- A transistor is a semiconductor gadget used to enhance or switch electronic signs, while a rationale entryway is a blend of semiconductors organized to play out a particular rationale capability.
- How would I begin finding out about logic gates?
- Begin with basic electronics textbooks, online tutorials, and interactive simulations to understand the principles and applications of logic gates.
BUSINESS
Why Businesses Benefit from Obtaining an LEI Certificate

In an interconnected financial landscape, businesses are increasingly required to get a Legal Entity Identifier (LEI) certificate. Businesses can benefit significantly from obtaining an LEI certificate through an accredited LEI Register. This unique identifier is crucial in regulatory compliance, risk management, and transparency within the global financial system. This listicle will explore why businesses can significantly benefit from obtaining an LEI certificate and how it enhances their operations and credibility.
Enhanced Regulatory Compliance
One of the primary benefits of obtaining an LEI certificate is enhanced regulatory compliance. Many regulatory authorities worldwide mandate using LEIs by entities engaged in financial transactions. Having an LEI ensures that businesses comply with these regulations, avoiding potential penalties or restrictions on conducting certain transactions.
Facilitates Global Transactional Activities
Businesses with an LEI certificate can seamlessly engage in global transactional activities. LEIs are recognized and accepted internationally, allowing businesses to participate more efficiently in cross-border trades, securities transactions, and other financial activities. Having an LEI eliminates the need for multiple identifiers across different jurisdictions, streamlining operations.
Improves Transparency and Market Trust
LEIs contribute to improved transparency and market trust by providing standardized and accurate identification of legal entities involved in financial transactions. Investors, regulators, and counterparties can easily access LEI data to verify entity details, ownership structures, and compliance status. This transparency provides trust and confidence in the integrity of financial markets.
Streamlines Reporting and Compliance Obligations
Businesses with LEI certificates benefit from streamlined reporting and compliance obligations. Many regulatory reports and filings require LEIs to identify counterparties and participants in financial transactions. Having an LEI simplifies the reporting process, reduces administrative burdens, and ensures accurate data submission to regulatory authorities.
Supports Risk Management Practices
LEIs play a crucial role in supporting effective risk management practices within organizations. By accurately identifying legal entities involved in transactions, LEIs enable businesses to assess counterparty risks more effectively and implement risk mitigation strategies. LEIs contribute to overall operational resilience and financial stability.
Ensures Access to Financial Services
Obtaining an LEI certificate ensures businesses have continued access to financial services and market opportunities. Many financial institutions, trading platforms, and counterparties require businesses to have active LEIs to initiate transactions or open accounts. Businesses with LEIs can leverage a broader range of financial services and investment opportunities.
Embracing Global Standards
Obtaining an LEI certificate ensures compliance with local regulations and demonstrates a commitment to global standards and best practices in financial reporting and transparency. LEIs are recognized and accepted across jurisdictions, providing businesses with a standardized identifier that facilitates cross-border transactions and regulatory compliance. Embracing global standards through LEI adoption strengthens businesses’ reputations in the international marketplace.
Fostering Trust and Confidence
An LEI certificate fosters trust and confidence among stakeholders, including investors, customers, and business partners. The transparency and accuracy provided by LEIs instill assurance that businesses are legitimate entities with verified information. This transparency reduces uncertainties and enhances businesses’ credibility in the eyes of market participants. By obtaining an LEI certificate, businesses signal their commitment to transparency and integrity, building stronger relationships and opportunities within the financial ecosystem.
From enhanced regulatory compliance and global transactional capabilities to improved transparency and market trust, LEIs contribute to streamlined operations and credibility within the financial industry. By embracing LEI adoption, businesses can position themselves for success in an evolving global economy. Ensure your business remains compliant and competitive by obtaining an LEI certificate through a trusted LEI Register and unlocking the full range of benefits it offers to businesses worldwide.
REAL ESTATE
The Power of Assurance: How Performance Bonds Benefit Contractors and Clients?

In the world of construction, trust is paramount. Contractors and clients seek assurance that projects will be completed satisfactorily, on time, and within budget. This assurance is where a performance bond comes into play. These bonds offer security for both parties involved in a construction project, ensuring that contractual obligations are fulfilled. Understanding their significance is crucial for anyone engaged in the construction industry.
A Safety Net for Project Success:
It is a three-way agreement between a client (the obligee), a contractor (the principal), and a surety company. The surety company issues the bond, providing the client with financial compensation if the contractor does not fulfill the project requirements outlined in the contract. This includes meeting deadlines, adhering to quality standards, and staying within the agreed-upon budget.
Think of this as a safety net. If the contractor encounters unforeseen circumstances that prevent them from fulfilling their contractual obligations, the client has recourse. They can file a claim against the bond, and the surety firm will step in to cover the costs of completing the project or compensate the client for any damages incurred.
Benefits for Clients:
It offers clients a significant layer of security and peace of mind. Here’s how:
Financial Protection: The biggest advantage is undoubtedly financial protection. If a contractor defaults on their obligations, the client may bear the expenses associated with rectifying substandard work, engaging a new contractor to finalize the project, or managing any resulting delays. The surety company assumes that financial burden.
Reduced Risk: These bonds eliminate the risk associated with contractor insolvency or unforeseen circumstances. Even reputable contractors can face challenges, and a bond ensures the project is completed.
Improved Quality: Knowing that their performance is guaranteed financially incentivizes contractors to deliver high-quality work. The prospect of a claim against the bond motivates them to adhere to strict quality standards throughout the project.
Stronger Bidding Process: By requiring this bond, clients attract more qualified and experienced contractors who are confident in their ability to deliver. This fosters a more competitive bidding process, potentially leading to better pricing and project outcomes.
Benefits for Contractors:
These aren’t just beneficial for clients. Contractors can leverage them to:
Demonstrate Credibility: Obtaining a bond signifies financial stability and a commitment to ethical business practices. This strengthens a contractor’s reputation and gives them a competitive edge when bidding on projects.
Access Larger Projects: Many large-scale projects mandate these bonds as a prerequisite for bidding. Having a bond allows contractors to compete for these lucrative opportunities and expand their business reach.
Build Stronger Client Relationships: It displays a contractor’s determination to complete projects on schedule and under budget. This fosters trust and strengthens client relationships, leading to repeat business and positive word-of-mouth recommendations.
Peace of Mind: It also offers a sense of security for contractors. Knowing that the client has financial recourse in case of unforeseen delays or complications can ease anxieties and allow them to focus on delivering quality work.
Considerations and Costs:
While these bonds offer undeniable advantages, there are a few things to consider:
Cost: The cost varies depending on the project size, complexity, and the contractor’s financial history. Typically, it ranges from 1% to 3% of the total contract value.
Selection Process: The surety company must thoroughly evaluate the contractors before securing this bond. Contractors must submit financial statements, project plans, and references to demonstrate their ability to fulfill the contract.
Claim Process: In the event of a claim, the surety company will investigate the situation thoroughly before compensating the client. Open communication and clear documentation are crucial for a smooth claims process.
Summing it Up:
A performance bond is vital in fostering trust and mitigating risk in the construction industry. They offer peace of mind to clients and contractors, ultimately contributing to the successful completion of projects. By understanding the benefits and considerations involved, clients seeking reliable contractors and contractors looking to expand their business opportunities can leverage the power of these bonds to achieve their goals.
BUSINESS
8 Effective Technology Strategies For Small Businesses

In today’s rapidly evolving digital landscape, technology has become a vital tool for small businesses striving to compete and thrive. From enhancing operational efficiency to improving customer engagement, the right technology strategy can make a significant impact on the success of a small business.
However, navigating the complex world of technology can be daunting, especially for small business owners who may not have the resources or expertise of larger enterprises. That’s why developing and implementing effective technology strategy is crucial for small businesses looking to stay ahead of the curve. Managed IT Services Springfield experts specializes in providing effective technology strategies to small businesses.
This article will explore the most effective business IT strategies.
8 Effective Technology Strategies For Small Businesses
1. Utilize Cloud-based Solutions
Cloud-based solutions offer small businesses a cost-effective and efficient way to manage their operations. With cloud technology, companies can access their data and applications from anywhere with an internet connection, providing flexibility and scalability. Cloud-based solutions also offer enhanced security measures to protect sensitive business information, reducing the risk of data breaches.
These solutions often come with automatic updates and backups, ensuring that businesses are always up-to-date and prepared for any unforeseen circumstances. Embracing cloud-based technologies can help small companies streamline their processes, improve collaboration among team members, and stay competitive in today’s digital landscape.
2. Leverage Data Analytics
Data analytics can be a powerful tool for small businesses seeking insights and making informed decisions. By leveraging data analytics, companies can analyze trends, customer behavior, and operational performance to identify opportunities for growth and improvement.
Small businesses can use data analytics to track key performance indicators, optimize marketing strategies, and improve overall efficiency. Implementing a data analytics strategy can help small businesses stay competitive in today’s fast-paced market by enabling them to make data-driven decisions that drive success and profitability.
3. Adopt Mobile Technology
Small businesses looking to enhance their operations and reach a wider customer base should consider adopting mobile technology as a key component of their strategic approach. Integrating mobile devices, applications, and services into daily business can improve efficiency, communication, and productivity.
By leveraging mobile technology, small businesses can streamline processes, provide better customer service, and stay ahead in an increasingly competitive market. Whether implementing mobile payment solutions or developing a mobile-friendly website, embracing mobile technology is essential for small businesses aiming to thrive in today’s digital landscape.
4. Implement Security Measures
Implementing security measures is crucial to safeguarding sensitive data and protecting against cyber threats when it comes to IT business strategies. Small businesses are increasingly becoming targets for cyber attacks, making it essential to prioritize cybersecurity.
Some effective security measures include setting up firewalls, using encryption tools, regularly updating software and systems, implementing strong password policies, conducting employee training on cybersecurity best practices, and investing in antivirus software. Visit IT Support Portland experts to minimize the risk of data breaches and ensure the confidentiality and integrity of the business operations.
5. Implement Remote Work Policies
Implementing remote work policies can be strategic for small businesses looking to enhance productivity and flexibility. Companies can reduce overhead costs associated with maintaining a physical office space by allowing employees to work from home or other off-site locations. Remote work policies also open up opportunities for hiring talent beyond local geographic boundaries, increasing the potential pool of skilled workers.
To effectively implement remote work policies, businesses should establish clear communication, task management, and data security guidelines to ensure seamless operations and maintain high productivity levels among remote teams. Regular performance evaluations and feedback mechanisms can help monitor the effectiveness of remote work arrangements and make necessary adjustments to optimize workflow efficiencies.
6. Stay Up-to-date on the Latest Trends
Staying up-to-date on the latest technology trends is crucial for small businesses looking to remain competitive in today’s fast-paced digital landscape. Small companies can identify opportunities to streamline operations, improve customer experiences, and drive growth by keeping abreast of technological advancements.
Whether embracing cloud computing, adopting automation tools, or leveraging data analytics, staying informed about emerging technologies can help small businesses decide where to invest their resources for long-term success. Regularly assessing your business’s technological needs and seeking guidance from IT professionals can ensure that your business stays ahead of the curve and maximizes its potential for success in the ever-evolving digital age.
7. Focus on Customer Experience
Focusing on customer experience is crucial for small businesses looking to succeed in today’s competitive business landscape. By prioritizing the customer journey and ensuring seamless interaction at every touchpoint, companies can build trust, loyalty, and satisfaction among their customer base.
Implementing technology-driven solutions such as customer relationship management (CRM) systems, chatbots for instant support, and personalized marketing strategies can enhance the overall customer experience. Small businesses that prioritize customer experience are more likely to retain customers, attract new ones through positive word-of-mouth, and ultimately drive growth and success in the long term.
8. Exploiting Marketing Technologies for Growth
Leveraging marketing technologies can be a game-changer for small businesses’ growth and success. Marketing technologies allow small businesses to reach a wider audience, engage with customers more effectively, and streamline their marketing efforts.
Small businesses can make informed decisions, track progress, and optimize their marketing strategies by utilizing customer relationship management (CRM) software, email marketing platforms, social media management tools, and analytics software. Implementing these technologies strategically can help small businesses stay competitive in today’s digital landscape and drive sustainable growth.
Real estate professionals, in particular, can benefit greatly from identifying the Best CRM for Real Estate Agents, which can streamline their operations and improve client interactions.
In Conclusion
Small businesses can significantly benefit from implementing effective technology strategies. By prioritizing digital transformation, leveraging cloud services, ensuring cybersecurity measures, and fostering a culture of innovation, small businesses can enhance their competitiveness, improve operational efficiency, and better meet the evolving needs of their customers. It’s crucial to stay informed about emerging technologies and trends and to tailor IT strategies for businesses to align with their unique goals and challenges. With the right approach, technology can be a powerful enabler of growth and success for small businesses in today’s digital age.

 BUSINESS1 year ago
BUSINESS1 year agoExploring the Benefits of Commercial Printing

 HOME IMPROVEMENT12 months ago
HOME IMPROVEMENT12 months agoThe Do’s and Don’ts of Renting Rubbish Bins for Your Next Renovation

 BUSINESS12 months ago
BUSINESS12 months agoBrand Visibility with Imprint Now and Custom Poly Mailers

 HEALTH8 months ago
HEALTH8 months agoThe Surprising Benefits of Weight Loss Peptides You Need to Know

 TECHNOLOGY10 months ago
TECHNOLOGY10 months agoDizipal 608: The Tech Revolution Redefined

 HEALTH7 months ago
HEALTH7 months agoYour Guide to Shedding Pounds in the Digital Age

 HOME IMPROVEMENT8 months ago
HOME IMPROVEMENT8 months agoGet Your Grout to Gleam With These Easy-To-Follow Tips

 HEALTH11 months ago
HEALTH11 months agoHappy Hippo Kratom Reviews: Read Before You Buy!












